Listen up, tech enthusiasts! If you're into IoT (Internet of Things) and want to securely connect your remote devices using P2P SSH on Ubuntu, you're in the right place. This guide will walk you through everything you need to know about setting up a secure connection for your IoT devices. No more worrying about hackers or unauthorized access. We've got your back!
Connecting IoT devices remotely can be tricky, but with the right tools and methods, it's totally doable. Securely connect remote IoT P2P SSH Ubuntu is the holy grail of modern-day networking. Whether you're a seasoned pro or just starting out, this guide will give you the confidence to set up your system like a boss.
So, buckle up! We're diving deep into the world of SSH, P2P connections, and Ubuntu configurations. By the end of this, you'll be able to secure your IoT devices like a pro. Ready? Let's get started!
Read also:Chris Motionless Wife The Untold Story That Shook The Internet
Why Securely Connect Remote IoT P2P SSH Ubuntu Matters
In today's tech-driven world, securing your IoT devices is more important than ever. Imagine this: you've got a smart home system running on IoT devices, and someone hacks into it. Not cool, right? That's why learning how to securely connect remote IoT P2P SSH Ubuntu is crucial. It's not just about convenience; it's about keeping your data safe.
Understanding the Basics of SSH
SSH, or Secure Shell, is like a superhero for remote connections. It encrypts your data and ensures that your communication with remote devices remains private. When you're dealing with IoT devices, SSH becomes your best friend. It allows you to manage and control your devices from anywhere in the world without compromising security.
The Role of Ubuntu in IoT Security
Ubuntu is a popular choice for IoT enthusiasts because of its stability and security features. It's like the backbone of your IoT ecosystem. By using Ubuntu, you can set up a robust environment that supports secure connections and protects your devices from potential threats. Plus, it's open-source, which means you can customize it to fit your needs.
Setting Up SSH on Ubuntu for IoT Devices
Now that we understand why SSH and Ubuntu are important, let's dive into the setup process. Don't worry; it's not as complicated as it sounds. Follow these steps, and you'll have your SSH server up and running in no time.
- Step 1: Update your Ubuntu system by running the command
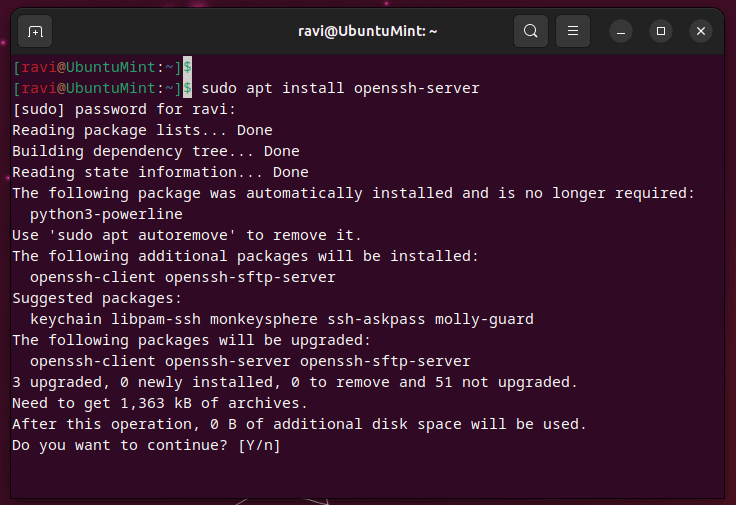
sudo apt update && sudo apt upgrade. - Step 2: Install the OpenSSH server using
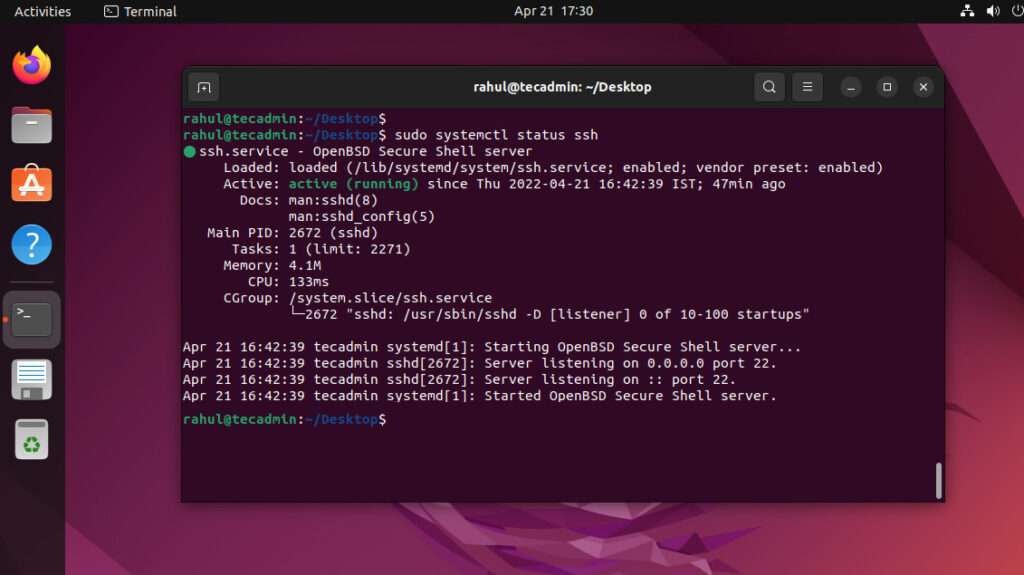
sudo apt install openssh-server. - Step 3: Check if the SSH service is running with
sudo systemctl status ssh. - Step4: Configure your firewall to allow SSH connections.
Once you've completed these steps, your Ubuntu system will be ready to handle secure SSH connections for your IoT devices. Easy peasy!
Creating a P2P Connection Between IoT Devices
Alright, let's talk about P2P connections. Peer-to-peer networking is like having a private chat between your IoT devices. It eliminates the need for a central server and makes your connections faster and more efficient. Here's how you can create a P2P connection:
Read also:Unveiling The Truth About Telegram Incest What You Need To Know
Step-by-Step Guide
Follow these simple steps to set up a P2P connection:
- Identify the IP addresses of your IoT devices.
- Use SSH to connect directly from one device to another.
- Configure your network settings to allow P2P communication.
- Test the connection to ensure everything is working smoothly.
With these steps, you'll have a secure P2P connection up and running in no time. Your IoT devices will thank you!
Tips for Securing Your IoT Devices
Security is key when it comes to IoT devices. Here are some tips to help you keep your devices safe:
- Change default passwords on all your devices. Don't be lazy about this!
- Enable two-factor authentication wherever possible.
- Regularly update your firmware and software to patch any vulnerabilities.
- Monitor your network for suspicious activity and take action if needed.
By following these tips, you'll significantly reduce the risk of unauthorized access to your IoT devices. Stay vigilant, my friend!
Understanding SSH Keys for Enhanced Security
SSH keys are like digital keys that unlock secure connections. They provide an extra layer of security by replacing traditional password authentication. Here's how you can generate and use SSH keys:
Generating SSH Keys
Run the following command to generate an SSH key pair:
ssh-keygen -t rsa -b 4096
This will create a public and private key pair. The public key can be shared with your IoT devices, while the private key should remain secure on your system.
Using SSH Keys
To use your SSH key for authentication, follow these steps:
- Copy the public key to your IoT device using
ssh-copy-id user@ip_address. - Test the connection by logging in with
ssh user@ip_address. - Disable password authentication to further enhance security.
With SSH keys in place, your connections will be more secure than ever!
Troubleshooting Common Issues
Let's face it: sometimes things don't go as planned. Here are some common issues you might encounter and how to fix them:
Issue 1: SSH Connection Refused
This usually happens when the SSH service isn't running or the firewall is blocking the connection. Double-check that the SSH service is active and ensure your firewall rules allow SSH traffic.
Issue 2: Permission Denied
This often occurs when the SSH key isn't properly configured. Make sure the public key is correctly added to the authorized_keys file on your IoT device.
By troubleshooting these issues, you'll be able to resolve most problems that arise during setup.
Best Practices for Managing IoT Devices
Managing IoT devices can be overwhelming, but with the right practices, it becomes a breeze. Here are some best practices to keep in mind:
- Document all your devices and their configurations.
- Set up monitoring tools to keep an eye on your network.
- Regularly back up your data to prevent loss.
- Create a routine maintenance schedule to keep everything running smoothly.
By following these best practices, you'll ensure that your IoT devices remain secure and functional.
Future Trends in IoT Security
The world of IoT is evolving rapidly, and so is the field of security. Here are some trends to watch out for:
1. AI-Powered Security
Artificial intelligence is being used to detect and respond to threats in real-time. It's like having a personal security guard for your IoT devices.
2. Blockchain Technology
Blockchain is being explored as a way to secure IoT communications. Its decentralized nature makes it ideal for P2P connections.
Stay ahead of the curve by keeping up with these trends and integrating them into your IoT setup.
Conclusion
There you have it, folks! A comprehensive guide on how to securely connect remote IoT P2P SSH Ubuntu. By following the steps outlined in this article, you'll be able to set up a secure and efficient IoT ecosystem. Remember, security is key, and taking the time to configure your system properly will save you a lot of headaches down the line.
So, what are you waiting for? Get out there and start securing your IoT devices. And don't forget to share this article with your fellow tech enthusiasts. Together, we can make the world of IoT a safer place!
Table of Contents
Why Securely Connect Remote IoT P2P SSH Ubuntu Matters
Setting Up SSH on Ubuntu for IoT Devices
Creating a P2P Connection Between IoT Devices
Tips for Securing Your IoT Devices
Understanding SSH Keys for Enhanced Security
Best Practices for Managing IoT Devices